
Authentication has become an essential part of the cybersecurity toolkit for the CISO. But in the new world of cloud applications and networks without perimeters, what is the role for Multi-Factor Authentication? We asked leading IT professionals for their view.
The inexorable rise of digital connectivity and the ubiquity of devices is producing ever-increasing volumes of sensitive and personal data. For organisations, keeping that data secure, without affecting the productivity that is being driven by the digital revolution, is one of the biggest challenges for the IT department.
This transformation in how we access data at work has been built on an undoing of the traditional – from the old network perimeter (and access via VPN) for a small number of users working at home. As this access extended to mobile and flexible workers, authentication became essential in helping to manage user security.
“It has been found that, on average, individuals have 26 different logins but only 5 different passwords”.
Experian
The Username-and-Password method as secure access was widely replaced with VPN connections, and yet, as the number of applications in which user access increased, it remained an essential part of the user experience, especially for on-premise applications. The assumption of local users being more secure meant that the inconvenience of authentication was rarely considered. To add, the move to the cloud has actually taken that assumption, rather than reverting to the best practice of an additional security layer.
So, is the cloud fully trusted? On top of this, how can a secure authentication model be translated to embrace the flexibility of cloud applications and the better user experience it offers? We reached out to hundreds of CIO, CISO and IT leaders to ask them about how authentication can bring the divide between security and productivity.
Securing someone else’s cloud
It cannot be forgotten that public clouds are often just that – public. Those applications which are well known and accessible to anyone with an internet connection and credentials are still intrinsically tied to email addresses. When a password is the only defence against stolen credentials and unfettered access, it’s time to re-evaluate the approach.

Usernames and Passwords have prevailed for a number of reasons, including convenience, speed of deployment, flexibility and cost. However, the biggest reason is perhaps user experience, as we all understand how this system works (no matter our own challenges in remembering long complex passwords that are unique to every site and application). Our technology ecosystem even drives this behaviour, not least browsers remembering passwords for us. The movement of traditionally consumer applications (such as Dropbox) into the corporate environment has also brought ease of use as a user expectation.
It’s also often the product of shadow IT and BYOD; as departments increasingly purchase applications and services outside of the IT department and rogue devices consequentially appear (such as the CEO’s iPhone), an all-encompassing approach to user identity management and security is very hard to apply.
Survey Results

Firstly, the use of Two Factor Authentication (or 2FA/MFA) within organisations is high at 62%, showing the majority of respondents deploying the technology within the organisation. The increased focus on the user, and their role at the forefront of cybersecurity defences, highlights the importance of validating their identity, while the user experience has improved alongside general familiarity with the technology (especially with 2FA used for personal banking or to validate cloud accounts with major email/social platforms).
However, over a third of respondents (38%) don’t use 2FA, showing that many organisations have yet to be convinced.
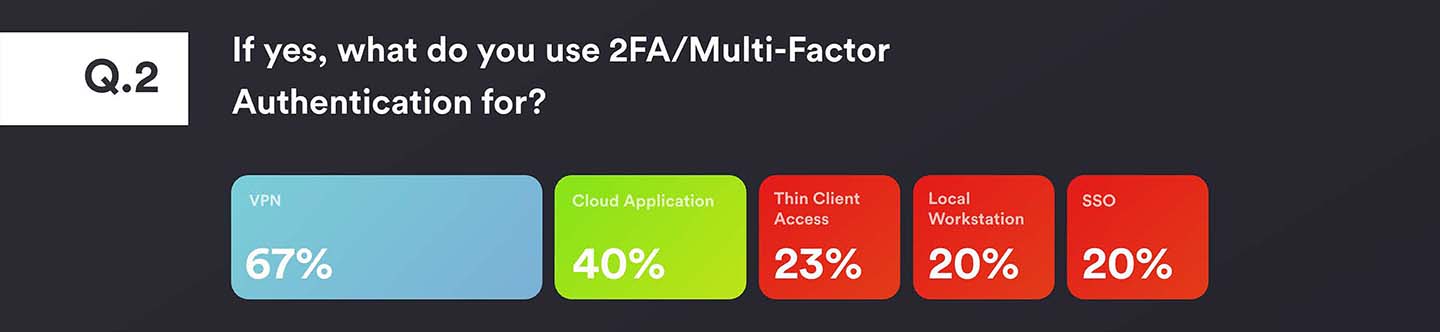
For those organisations using authentication, the highest use case by far was for VPN at 67% or remote access for mobile workers. This has traditionally been the main driver for authentication, focused around securing the traditional network perimeter. The second most popular use was for cloud applications, which indicates the recognition of their growth in helping drive digital transformation projects, flexible performance, and a move to more dynamic IT enablement and away from the complexity of on-premise infrastructure.
Importantly, even when deploying the hugely popular Office 365 suite, it’s not just about using applications like Outlook or Word; the most popular usage was OneDrive for file storage, making security even more important to validate identity. Less popular uses were thin clients, workstations and SSO. VDI remains a minority technology for many organisations, while SSO brings great potential around user experience, but is often viewed as a lower priority when budgets are defined.
Significantly, the results also show that organisations using authentication deploy it for multiple use cases – not just one. Being able to leverage technology in more than a single application can significantly increase ROI.

For all survey participants, a huge majority see their use of 2FA increasing to more applications or other use cases. This is covered by existing 2FA deployments and net new ones, which follow general market trends and the increase of drive towards improving security around user identity.

It is clear that mobile tokens are the most commonly used form of authentication (at 75%), and interestingly, the data suggests that almost all organisations don’t use multiple methods. Hardware tokens – the longest-running offering – have declined to just 27%, with the convenience of mobile tokens clearly being a key driver in helping meet user demands. Screen challenges are the most recent offering and are already equalling physical tokens.
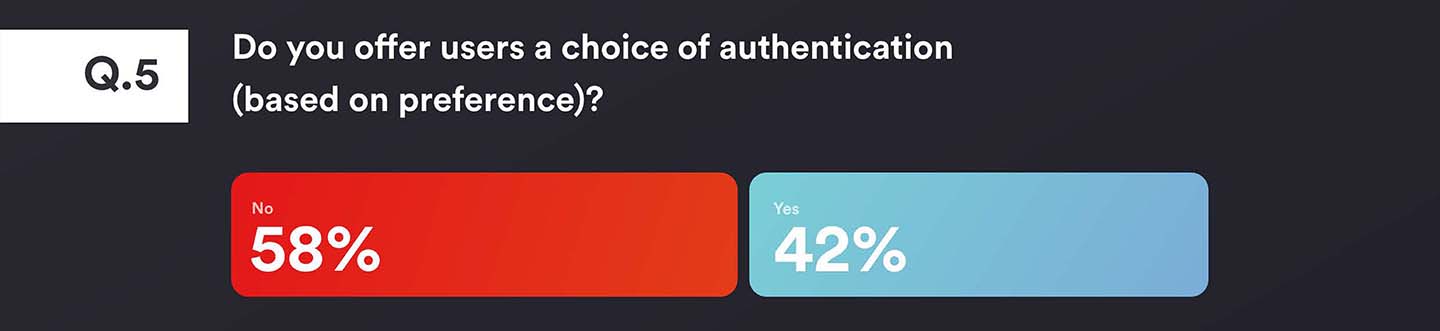
Although most end-users do not offer a choice of authentication based on preference (58%) , there is a significant number of those who do (42%), highlighting how important it is to show that providing a positive user experience is key in driving adoption and reducing the soft costs of authentication deployment (such as support calls).
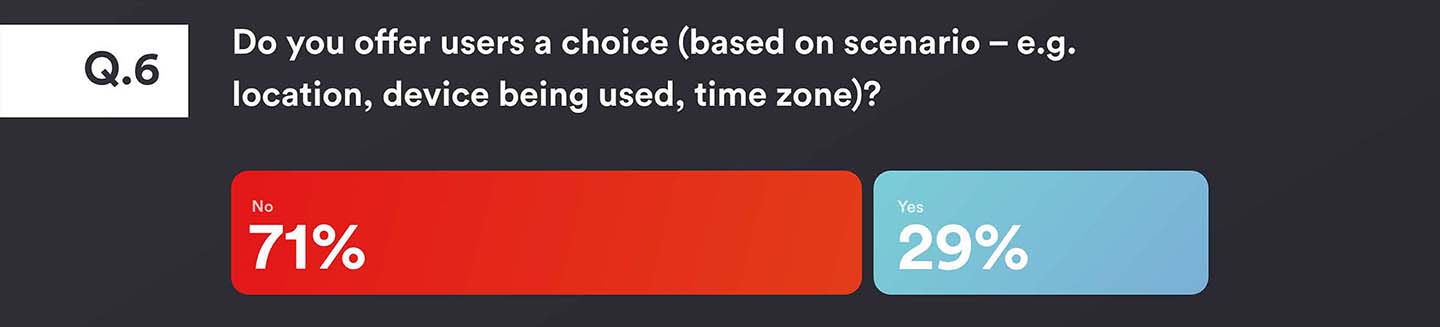
While offering users a choice is almost split 50/50, doing so in a dynamic way based on the specific use case scenario (such as the device being used, or what their location is) is significantly reduced. Just over a quarter (29%) offer it, meaning that for the rest, users are faced with having additional authentication requirements regardless.

The user experience is clearly an important element to many organisations, understanding that their staff are the front line of cybersecurity. They’re also aware that ensuring buy-in with any technology is dependent on delivering a simple, engaging user experience. This increases usage and reduces the chance of staff working around the problem, or increasing costs through additional support calls when things go wrong. Cost is the second most popular factor, recognising the limitations of budgets and the need for a cost-effective solution.
Having the option of a range of tokens is the second most popular requirement at 62%, yet only 42% currently have it. This suggests that there is a strong market demand for products that offer a more flexible approach. Ease of management and deployment options quickly follow, the latter again highlighting that the legacy approach of on premise (or a secondary option of public cloud) may not be sufficient for many.
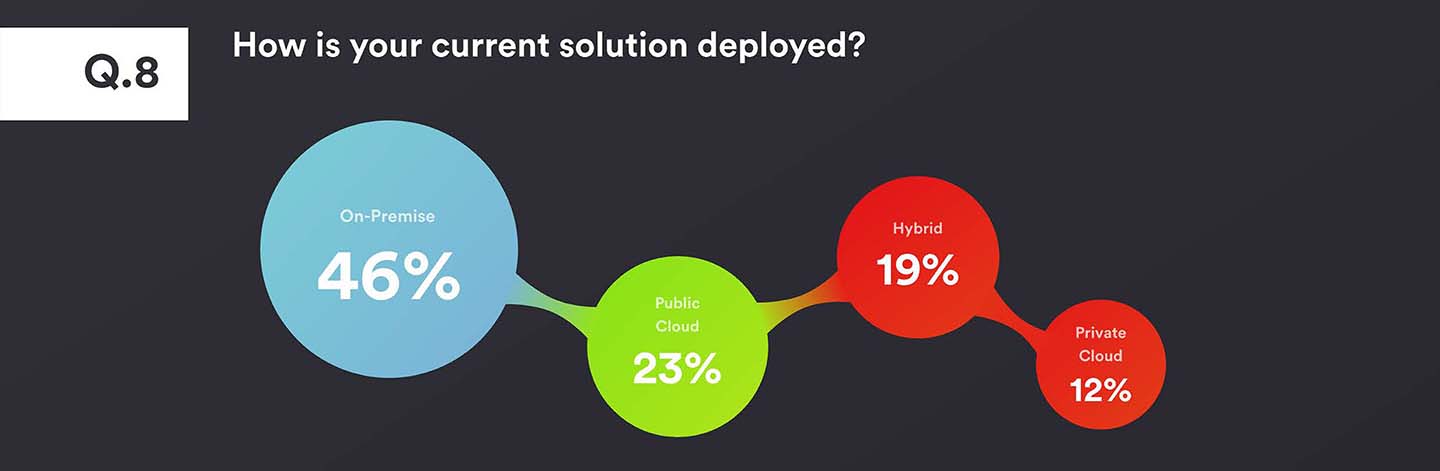
The majority of respondents still have on-premise authentication solutions, which has been the preferred method for most legacy technologies. The newer arrivals in the market have often been deployed on public cloud (such as Amazon Web Services or Microsoft Azure), offering the quickest route to market. However, many organisations may have reservations, due to questions around data security or location (to ensure compliance with legislation such as GDPR). Private Cloud is the least common, but this may be due to few companies providing it as an option.
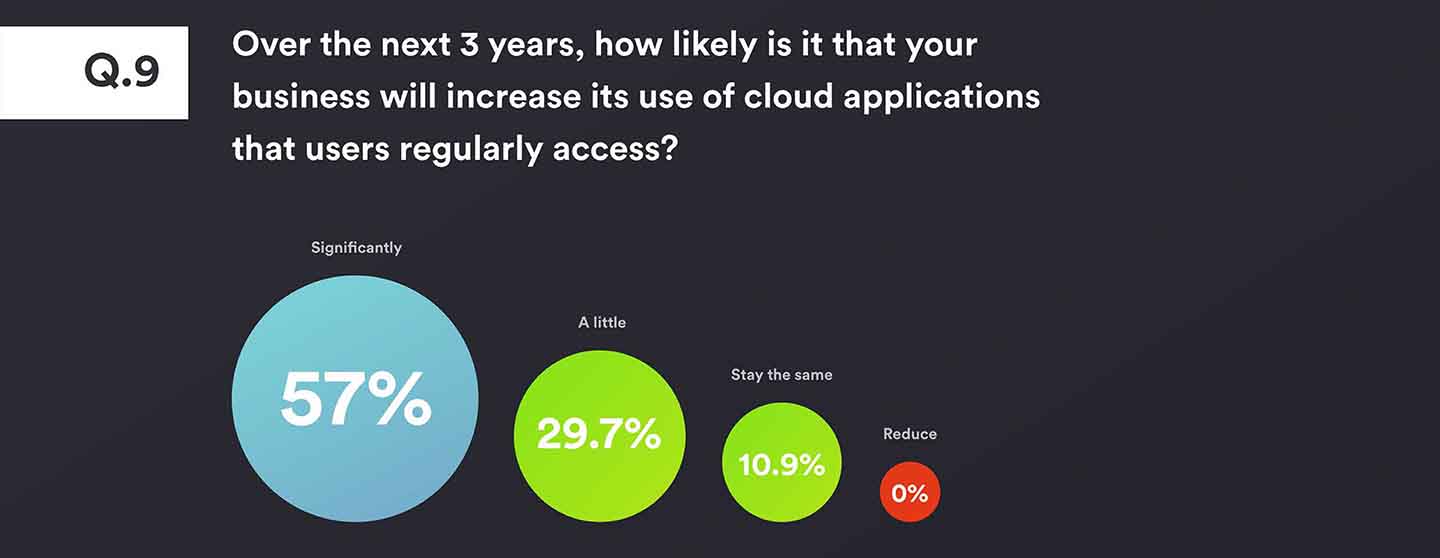
Overwhelmingly, organisations are looking to increase their level of cloud usage, and nearly two-thirds see that rise as being significant. Yet only 40% of respondents currently use authentication for cloud apps, and with the likes of Office365, Salesforce and Dropbox all containing copious amounts of customer and company data (both in terms of breadth and depth), many will surely be looking for additional layers of security to protect and secure access to it.
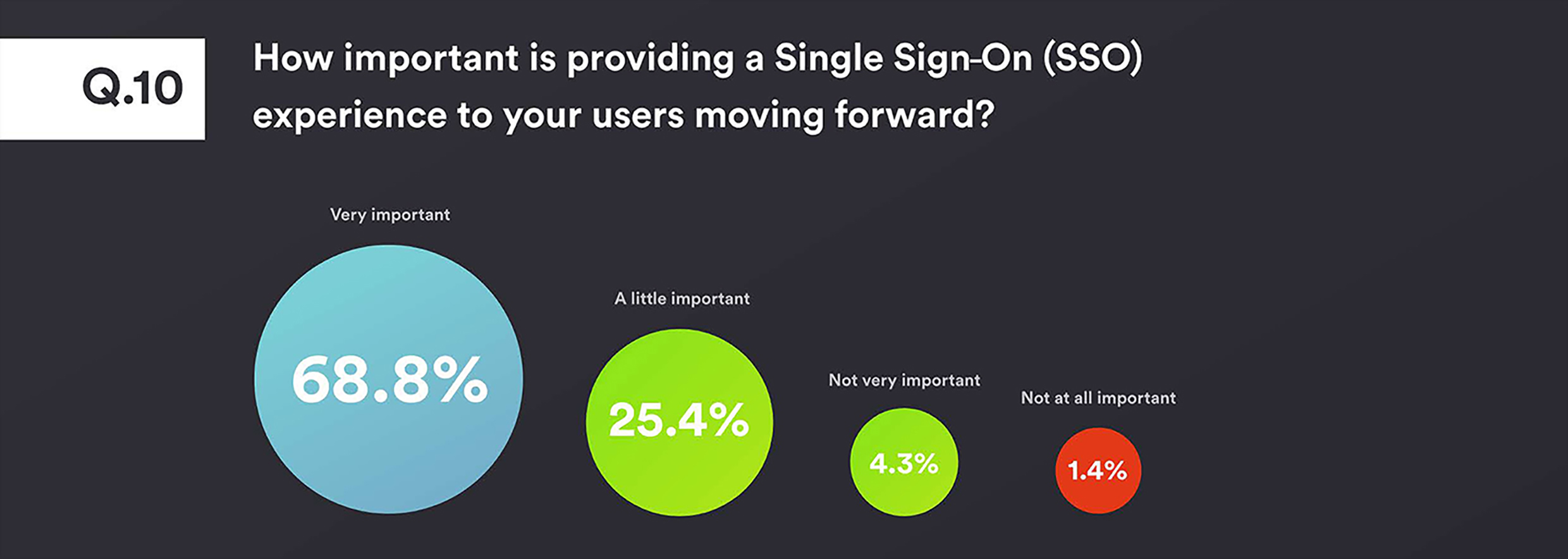
Similar to the findings that many organisations use cloud applications but don’t secure access with authentication, nearly 95% of respondents see Single sign-on(SSO) as an essential part of their IT strategy moving forward, and yet only 20% currently use it as part of their authentication deployment.
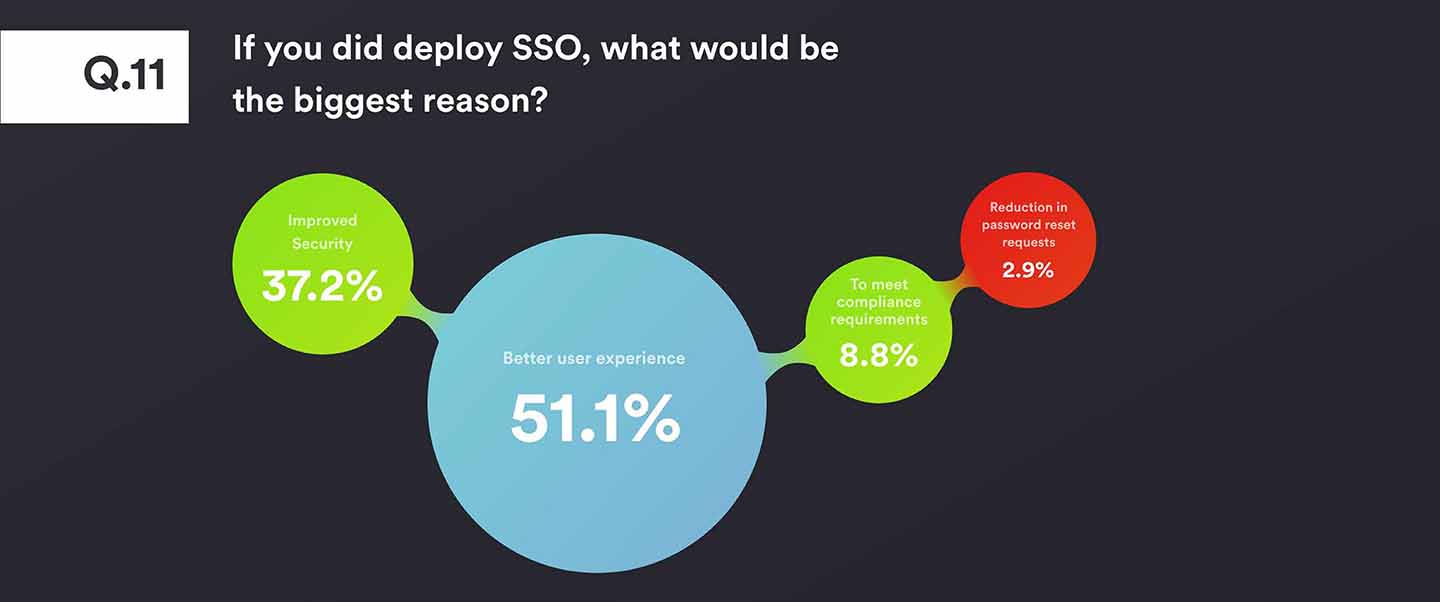
As a follow-up, we then asked what this strategy towards SSO would be driven by. Again, the user experience was key for over half the respondents. This was closely followed by better security, with compliance and a reduction in internal IT costs (such as reducing password reset requests) much lower down.
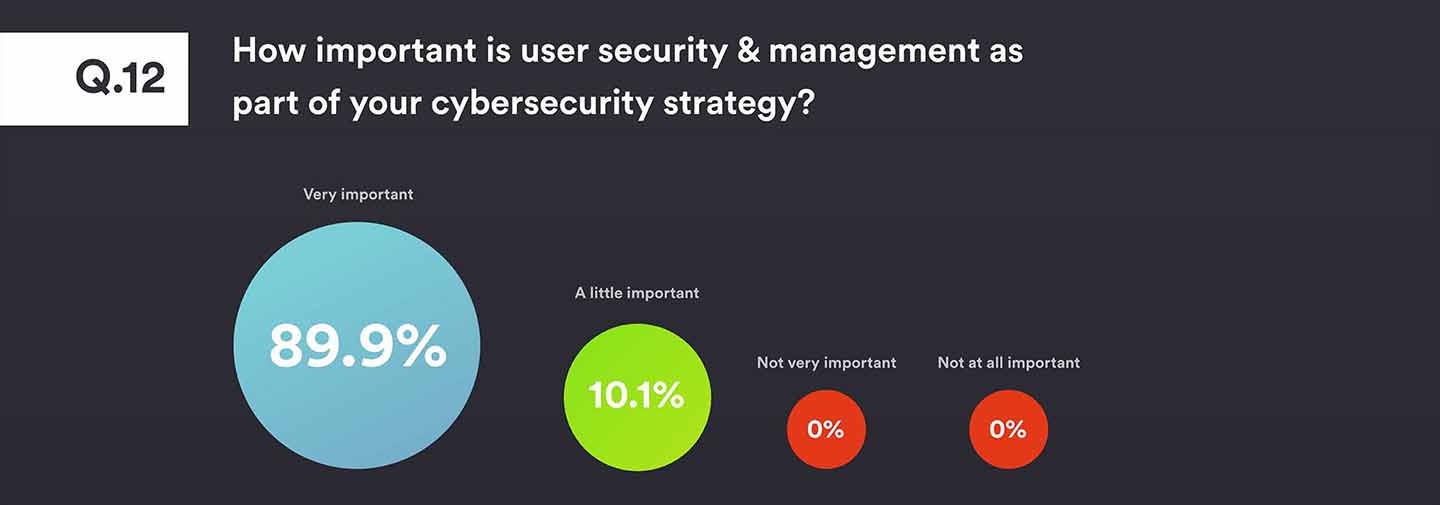
Initially, the overwhelming response to the importance of user security management as part of their cybersecurity strategy was that it plays a hugely important role. The challenge, of course, is how it can be effectively implemented.
Conclusion
Authentication as a technology has been part of many organisations’ cybersecurity strategies for many years. Traditionally relegated to the role of securing access to a VPN for remote workers, the explosion in cloud applications in the last 5 years has seen a growth in enterprises looking to embrace MFA as part of a wider move to user identity management. In the meantime, online services for consumers have made the technology more familiar for many, and the user experience in this field has helped drive the corporate adoption of mobile tokens and interactive challenges.
At the heart of the survey’s findings is the challenge of balancing user experience with security. Clearly, both ride at the top of priority lists, yet throughout, many organisations are looking towards a cloud-first approach and user-centric solutions whilst relying on legacy technology. The ‘digital transformation’ approach that is often at the heart of many IT strategies – currently being championed by CIOs – is designed to embrace the opportunities and unleash employee potential through IT. However, if access to these applications remains a challenge to manage and secure, then their success could ultimately be restricted.
The threat landscape for the modern CIO is forever changing, and the introduction of GDPR adds a significant legislative burden on protecting the data that is now increasingly spread across a local network, mobile devices and cloud applications. Ensuring that data is secured may be the primary focus, but providing access is the next step, and its level of security will define the success of the cybersecurity strategy. No one will want to compromise a positive user experience, but security demands will mean that a different approach is required.
This balance of user experience and security is central to risk-based authentication (RBA), which allows for the adaptation to the circumstances of the user’s access to a service through a set of policy rules. Therefore, every deployment will be unique to specific needs and risks. This results in a collaborative relationship between job role and IT functions, thus providing an essential educational tool to users which assists them in balancing security with productivity, as well as enforcing necessary controls.
Those rules could be in relation to the date/time, device, physical location, what service is being accessed and who the user is. Combining risk profiling with policy-based controls and a range of authentication methods (including PIN, SMS, image and mobile app) provides the most effective security possible that directly relates to the sensitivity and confidential nature of the data while providing a seamless experience for the user. It can even encompass compliance requirements (by data type, source or gee-location), ensuring that business processes are perfectly in-sync with the practical implementation of IT security policy, or portals that give the user the ability to change their PIN, password or self-provision the app, saving valuable IT staff time.
This approach enables organisations to embrace the flexibility of cloud applications, the productivity of a mobile workforce, and the productivity of technologies such as SSO and RBA while ensuring that an enterprise security policy is in place and an authentication solution can provide the first line of defence against the biggest threats.

