How to Secure your Public Data
How to effectively secure your public data
The government has a duty to protect its public data – ensuring confidential or sensitive information doesn’t reach the wrong hands.
But with cyberattacks becoming more sophisticated, it’s becoming increasingly difficult to secure data. The government is a prime target for data hacks, with opposition states and parties looking to expose secrets, and a sizable economic reward for successful ransomware attacks.
Incoming GDPR poses an additional problem – with any organization that’s responsible for protecting stakeholders’ data now having to prove that they’re putting measures in place to keep it secure.
It’s up to the IT staff at local councils, schools, and other government authorities to roll out security measures. However, when staff employed by the public sector, such as local government employees, are too busy to keep up with security best practice, and too reliant on current systems to risk overhauling, implementing any additional safety measures becomes a real challenge.
This article looks at the biggest challenges facing central and local government IT staff, and how you can protect your organization against these threats.
Securing existing systems
IT staff can face an uphill task making their data more secure, with their colleagues in a position where they don’t have time to add new processes to their workload or learn new systems. Data protection solutions need to cause as little disruption as possible. More often, IT staff look for ways to enhance their existing systems by improving their security, rather than replacing them with new software.
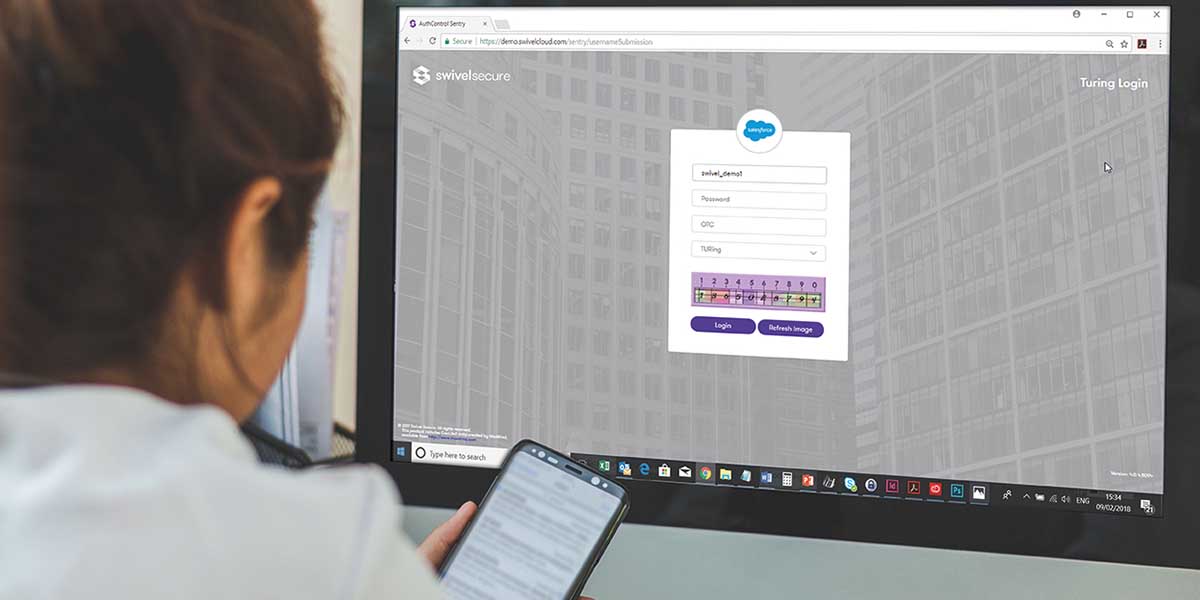
Multi-factor authentication (MFA) is a solution that requires multiple pieces of information for their identity to become authenticated. This may include something that the user knows, something that they have, or something that they are i.e. biometrics. However, although biometrics are unique to each such individual, they are not dynamic and do not benefit from one-time use. For example, using a PIN, pattern, or one-time code (OTC) that is only used once, makes authenticating more secure because it is always changing. An OTC is a simple but secure way of proving they are authorized to access the network, and only takes a few extra seconds.
Products like Swivel Secure’s AuthControl Sentry® integrates seamlessly with a number of applications like Salesforce – meaning government staff can continue to work in a way that is convenient for them, and they won’t have to learn new processes or systems.
MFA is convenient for internal councilors and external staff like healthcare workers, who can provision their mobile phones to provide a one-time code (OTC), so they can log on to a number of different services wherever their work requires.
In addition to OTCs, other encrypted authentication factors using the one-time use approach (PINpad or TURing image) provide employees with a way of authenticating securely, whatever device they are using and from wherever they are trying to gain access.
Keeping networks protected while staff work remotely
Within both central and local government, employees role’s are varied and do not always require staff to be office-based. For example, the responsibilities of local councilors and planning staff usually dictates that to perform their duties they need to visit development sites or meet with constituents within the community. This means they’re potentially logging on to the government network from a number of external locations and devices.
These hotdesking staff needs network access to be smooth and simple – but those responsible for network safety can have trouble keeping it protected without causing disruption. Assessing the risk of each individual log-in attempt is a difficult and time-consuming task for the IT department, with thousands of government staff signing in on devices every day.
Risk-Based Authentication (RBA) helps automate the process – letting you set up a number of rules for each application that will determine how safe the attempted log-in is. These rules can include the time and date of log-in, the device, IP address, and last authentication to enable you to give complete control over who can authenticate for the application.

Authenticating third-party access
It’s not just council staff working remotely that need to access the government network from different devices. External government staff like teachers and healthcare workers need to log in – and this can cause problems for those managing the network as it’s difficult to assess the risk of third-party users.
While RBA makes the process of risk management simpler for IT staff, it does mean that MFA users have to prove their credentials – adding an extra step to what should be a swift log-in task. Swivel Secure’s AuthControl Sentry® aims to make MFA effortless, without compromising network safety.
MFA can support both token and tokenless authentication, providing busy government employees and third parties with the flexibility of authenticating from a range of devices. Whether users are accessing applications through their desktop or mobile device, factors can be delivered in various dynamic formats including TURing or PINpad®, for optimum security.
Public Services Network
The Public Services Network (PSN) is designed to be a seamless platform for accessing and sharing resources across public sector organizations. It contains data from all government sectors, including local government, Police, and other authorities.
As the purpose of the network is to make sharing easier and promote efficiency, it’s a susceptible target for cyberattacks. If it was compromised, a hacker could move through the network and not only access the hacked user’s data – but any other data available.
Staff access to organizational documents through a private shared network can be secured using RBA. You can set criteria that determine the level of authentication users have to provide – from a username and password to PINpad password scrambling technology and mobile app authentication – depending on things like where they’re logging on from, their IP range, and more. This level of automated risk assessment keeps the network protected from unauthorized users.
GDPR
New data handling requirements have been introduced in the EU this year. General Data Protection Regulation (GDPR) means that any organization responsible for holding public data must prove that they’ve implemented reasonable measures in place to keep it protected. Government organizations hold data for thousands of people – so they need to be providing a high level of protection to their applications and data.
Technologies like Swivel Secure’s AuthControl Sentry® offer different types of authentication to suit all users. A mobile phone app option gives users an OTC that can’t be stolen and won’t be valid for more than that single log-in attempt. The PINpad® feature uses the PINsafe® technology – with each digit of your password corresponding to a different number on an image, so you never actually type in your real password. This also makes the technology impossible to hack using key-logging. Protecting your network and applications with products like these can help you start to become fully GDPR compliant.
Virtual Desktop Infrastructures
Staff working remotely may use a Virtual Desktop Infrastructure (VDI) to access their desktop set-up from a number of devices. VDIs are a virtual realization of a desktop – so organizations can equip them with all the resources staff need, and they can then access them from any location or device. This means staff can run legacy systems that wouldn’t usually be compatible with their modern laptop or PC.
It’s a hassle-free way of working – giving staff the tools they need, without asking them to carry a dedicated work device around. However, it also presents the typical risks of remote working. Organizations use VDIs to access and share files easily, so if access became compromised, the hacker could access all the information available across the virtual environment.
Authentication solutions that integrate with VDIs can keep your applications protected. Swivel Secure’s AuthControl Sentry® uses a simple one-time code to get staff up and running in seconds – and it can’t be stolen.
Virtual Private Network
In addition to protecting applications in a VDI environment, employees working in central and local government can benefit from the same dynamic authentication factors to protect their virtual private network (VPN) from unauthorized access.
Get more tips on how to secure your network and confidential data against online threats:





